Introduction
Understanding API Security
The Need for Multi-Layered API Security
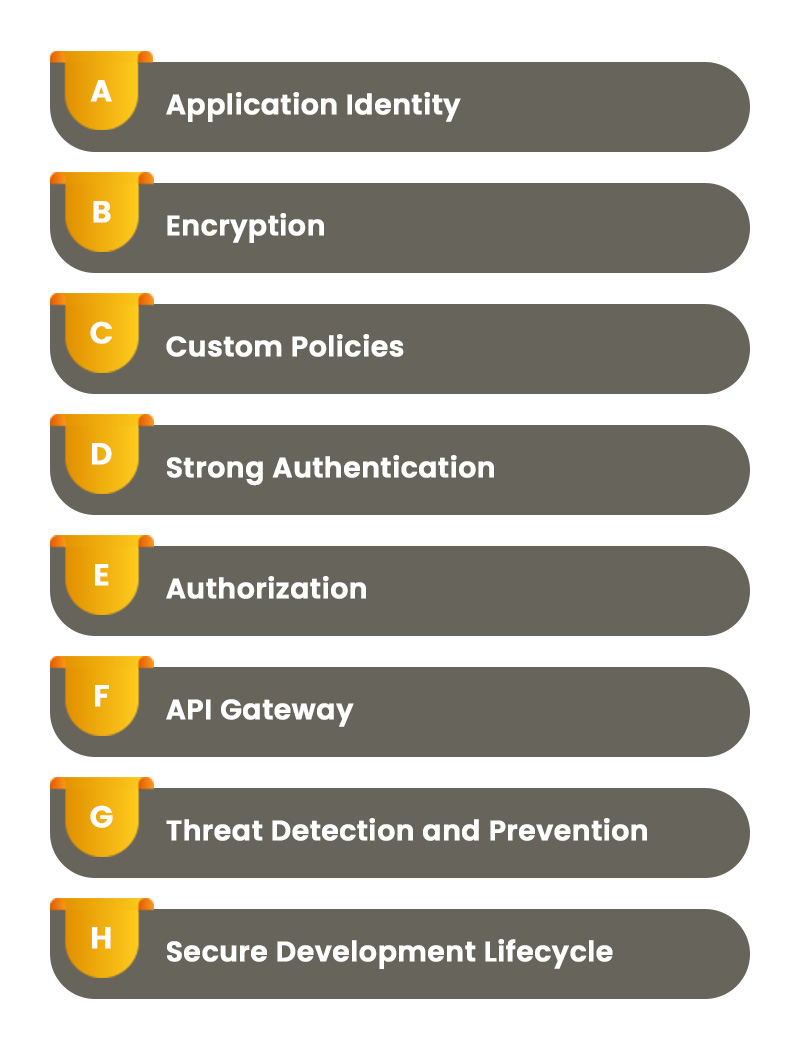
- Application Identity: Establishing a secure and unique identity for each API is vital. Application identity ensures that only trusted and authenticated applications can access the API's resources, preventing unauthorized access from malicious entities.
- Encryption: Implementing encryption for data transmission and storage is a fundamental aspect of API security. Encrypted data is rendered unreadable to unauthorized parties, ensuring data privacy and protection against eavesdropping attacks.
- Custom Policies: Designing and implementing custom security policies allows organizations to tailor their API security measures to specific use cases and risk profiles. Custom policies can include rate limiting, IP whitelisting, and payload validation to protect against brute force attacks and injection vulnerabilities.
- Strong Authentication: Enforce strong authentication mechanisms such as OAuth, API keys, or multi-factor authentication to ensure that only authorized users and applications can access the API's functionalities.
- Authorization: Establish granular access control to define what actions and resources each authenticated user or application can access. This ensures that sensitive data remains protected and only authorized entities can perform specific operations.
- API Gateway: Deploying an API gateway acts as a central point of control for API traffic, allowing organizations to enforce security policies, monitor API usage, and detect potential security breaches in real-time.
- Threat Detection and Prevention: Employ advanced threat detection tools to identify and block malicious activities, such as DDoS attacks or unusual patterns in API requests. Early detection and prevention can significantly reduce the impact of potential threats.
- Secure Development Lifecycle: Implement security measures from the very inception of API development. Adopting secure coding practices and conducting regular security audits during the development lifecycle helps identify and address vulnerabilities early on.
Common API Security Threats
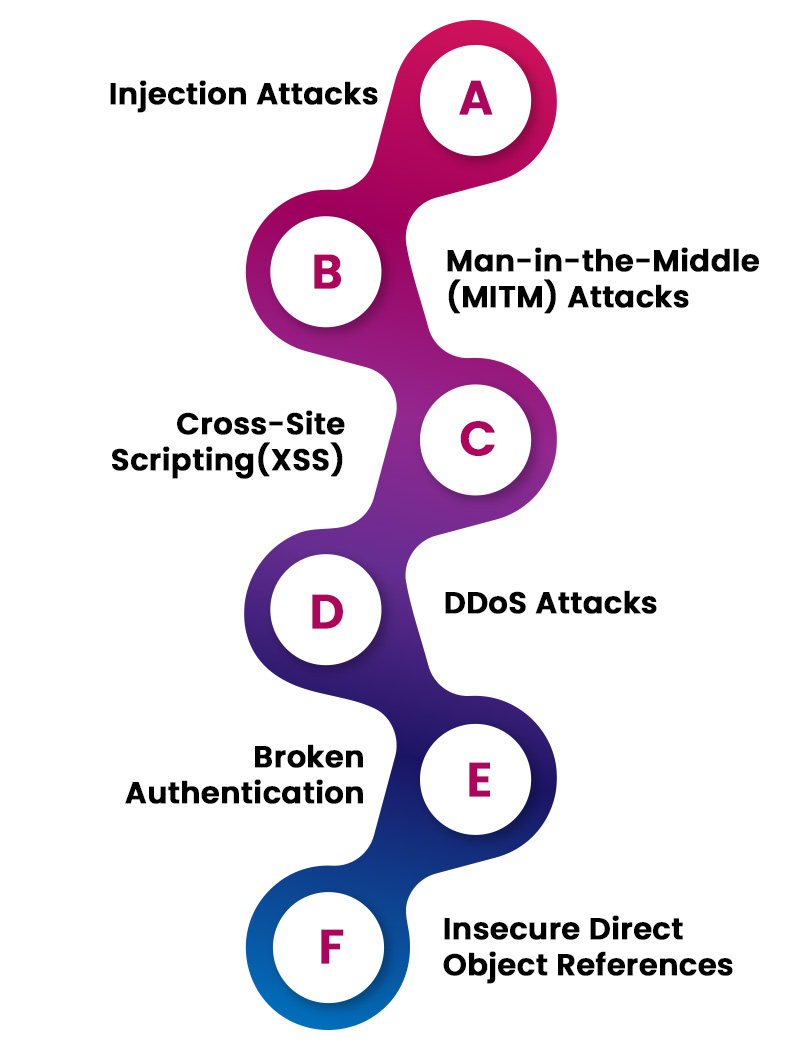
- Injection Attacks: Malicious actors exploit vulnerabilities in input fields to inject malicious code, leading to data breaches or unauthorized access.
- Man-in-the-Middle (MITM) Attacks: Attackers intercept communication between the client and server, eavesdropping on sensitive data transmitted over unsecured channels.
- Cross-Site Scripting (XSS): Hackers inject malicious scripts into web pages viewed by other users, enabling them to steal sensitive data or take control of user accounts.
- DDoS Attacks: Distributed Denial of Service attacks overwhelm the API server with a flood of requests, causing service disruptions and potential data breaches.
- Broken Authentication: Weak or insufficient authentication mechanisms enable unauthorized access to APIs and sensitive data.
- Insecure Direct Object References: Poorly implemented authorization allows attackers to manipulate object references and access unauthorized resources.
Building a Multi-Layered API Security Strategy
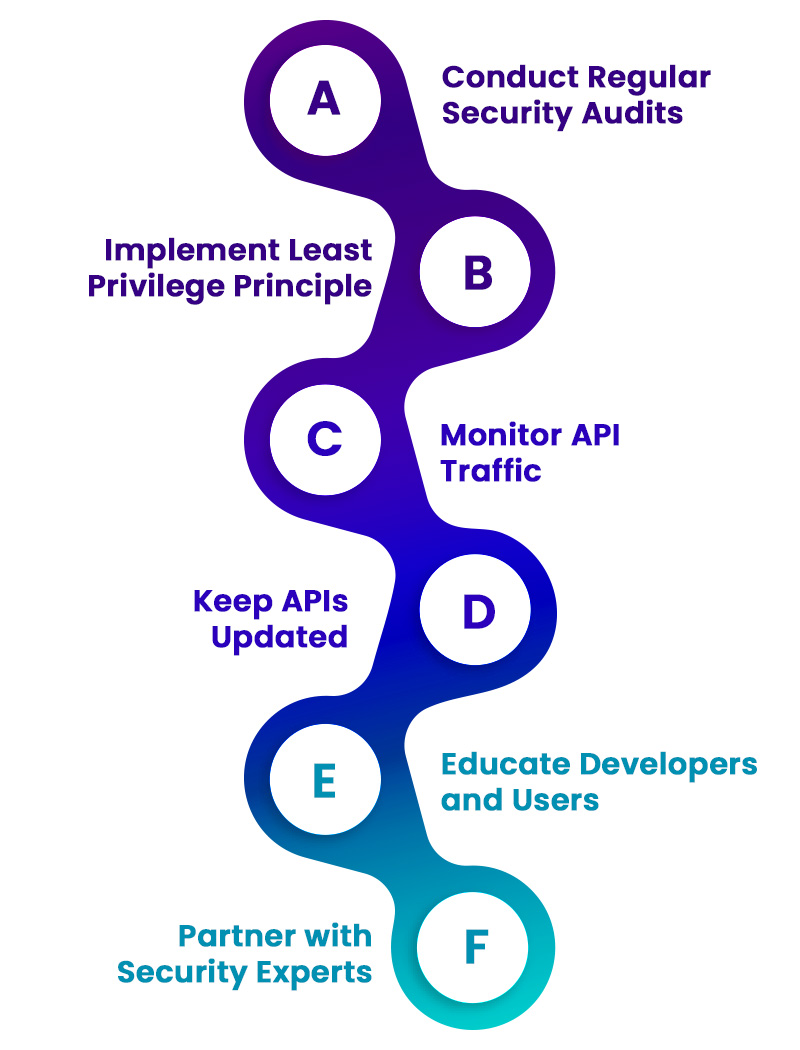
- Conduct Regular Security Audits: Perform periodic security assessments and penetration testing to identify and rectify vulnerabilities.
- Implement Least Privilege Principle: Grant the minimum level of access required to perform specific operations, reducing the potential damage caused by compromised accounts.
- Monitor API Traffic: Deploy real-time monitoring and logging to detect and respond promptly to suspicious activities.
- Keep APIs Updated: Regularly update APIs to patch security vulnerabilities and adopt the latest security features.
- Educate Developers and Users: Raise awareness among developers and users about API security best practices and potential threats.
- Partner with Security Experts: Collaborate with security experts and vendors to implement state-of-the-art security measures and stay updated on the latest security trends.
Conclusion
As APIs continue to empower digital innovation and business growth, the importance of multi-layered API security cannot be overstated. By implementing measures such as application identity, encryption, custom policies, strong authentication, and authorization, organizations can build a robust defense against potential cyber threats. A proactive and comprehensive approach to API security ensures the protection of sensitive data, maintains customer trust, and compliance with regulatory requirements.
Embracing a multi-layered API security strategy is not only a safeguard for the organization’s digital fortress but also a testament to the commitment to protect and secure the data and privacy of customers and stakeholders in an ever-evolving digital world.